differential power analysis tutorial
Introduction to differential power analysis. Figure 1 sho ws an SP A trace from a t ypical smart card as it p erforms a DES op eration.
Cryptography Free Full Text Power Side Channel Attack Analysis A Review Of 20 Years Of Study For The Layman Html
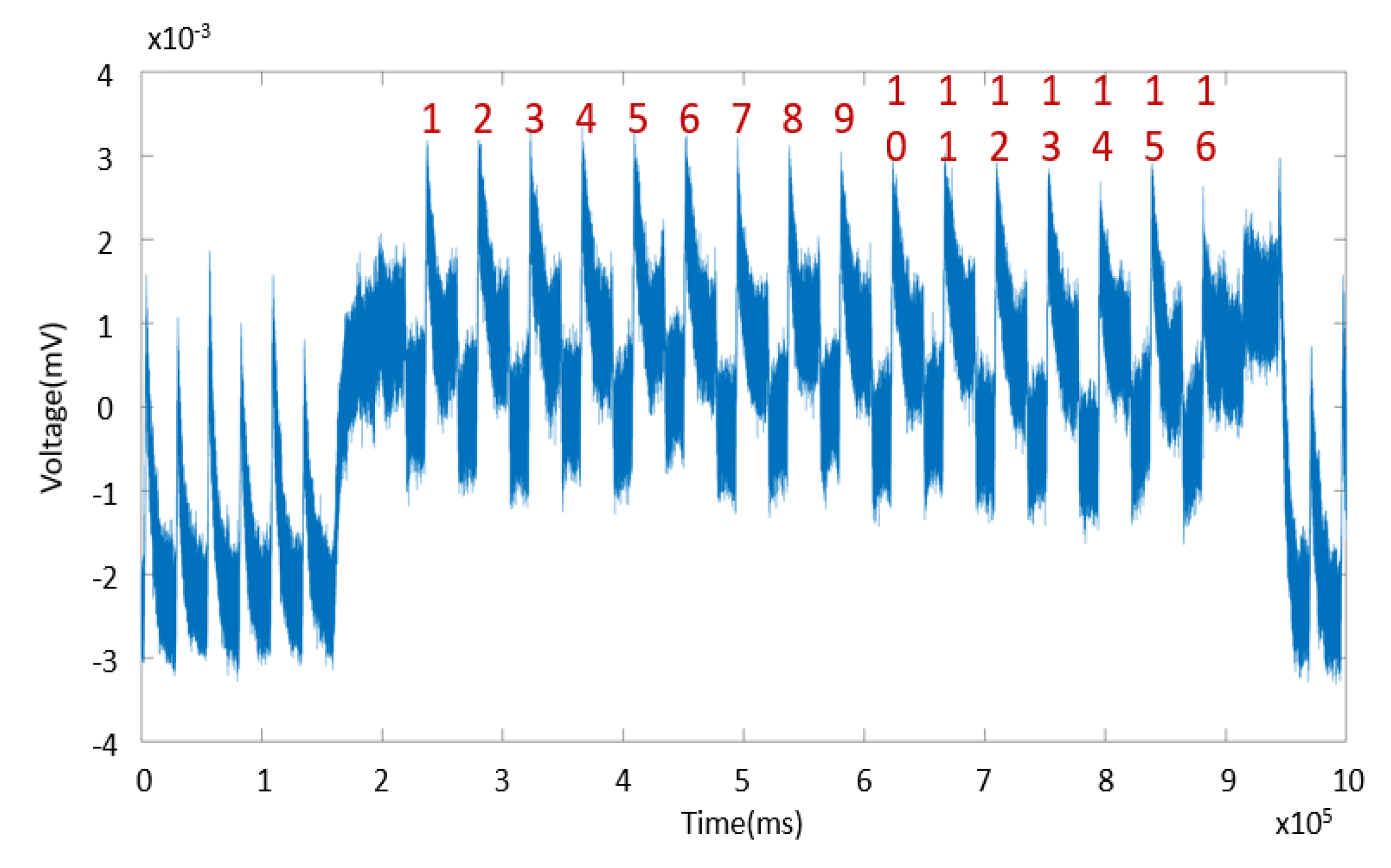
Figure 2 is a more detailed view of the same trace sho wing the second and 2 third rounds of a DES encryption op eration.

. When the attacker uses DPA he does not need any de-tailed knowledge of how the encryption algorithm was im-plemented. As a result measurements of the power used by actual computers or microchips contain information about the operations being performed and the data being processed. The basic method involves partitioning a set of traces into subsets then computing the difference of the averages of these subsets.
The first part of the tutorial Differential Power AnalysisKey Recovery is aimed at explaining the creation of the power hypothesis and the use of algebraic systems. The method does not attack the cipher but the physical implemen-tation of the cryptographic system. The second part of the tutorial DPAmeasurement with an oscilloscope covers the practical part of the exercisethe measurement of the power consumption using the PicoScope.
Toolbox for advanced differential power analysis of symmetric key cryptographic algorithm implementations. If the choice of which trace is. If the choice of which trace is.
Differential Power Analysis DPA is a powerful method for breaking the crypto-graphic system. Statistics and cryptography for the attack itself programming skills and experience in instrumentation to build up an automatic measurement system and electronical skills to. Linear-regression side-channel dpa cryptography-tools differential-power-analysis.
22 Differential power analysis Differential Power Analysis DPA is a statistical method for analyzing sets of measurements to identify data-dependent correlations. The first part of the tutorial Differential Power Analysis Key Recovery is aimed. This tutorial provides information on all these topics on basis of our experience.
Support six fully differential inputs or twelv e single-ended inputs The content of this tutorial is not Differential casing thermal analysis We choose a 4 core machine for the computation to have enough computing power for. In this paper we introduce differential powerful analy- sis DPA simple power analysis SPA as well as several relatedtechniquesTheseattacksleveragemeasurementsofa targetdevicespowerconsumptionorothersidechannelsto extractsecretkeysThemethodsareeffectiveagainstimple- mentations of all major algorithms. In this paper we introduce differential powerful analy- sis DPA simple power analysis SPA as well as several relatedtechniquesTheseattacksleveragemeasurementsofa targetdevicespowerconsumptionorothersidechannelsto extractsecretkeysThemethodsareeffectiveagainstimple- mentations of all major algorithms.
Performing a Differential Power Analysis DPA attack requires knowledge in several fields. Tutorial B2 Viewing Instruction Power Differences. The second part of the.
A complete introduction to side channel power analysis also called differential power analysis. Tutorial B5 Breaking AES Straightforward Tutorial B6 Breaking AES Manual CPA Attack. This is part of training available that will be available a.
Performing a Differential Power Analysis DPA attack requires knowledge in several fields. SP A trace sho wing DES rounds 2 and 3. Can be gained from the power consumed by the device electromagnetic radiation or the time taken to complete a computation 3.
Therefore even systems using modern strong. Updated on Sep 15 2018. Differential Power Analysis is more powerful than SPA.
There are three types of power analysis attacks simple power analysis SPA attacks differential power. ADuCM36x Getting Started Tutorial Noise analysis. About Press Copyright Contact us Creators Advertise Developers Terms Privacy Policy Safety How YouTube works Test new features Press Copyright Contact us Creators.
CiteSeerX - Document Details Isaac Councill Lee Giles Pradeep Teregowda. Statistics and cryptography for the attack itself programming skills and experience in instrumentation to build up an automatic measurement system and electronical skills to improve the results. This technique is also more powerful because it uses statistical analysis to get the side channel informa-tion.
Tutorial B11 Breaking RSA skip on Arm From there we will skip to Differential Power Analysis tutorials. Note that the 16 DES rounds are clearly visible. The basic method involves partitioning a set of traces into subsets then computing the difference of the averages of these subsets.
Power analysis attacks are used to gain sensitive information by monitoring the power consumption of the device. The first part of the tutorial Differential Power Analysis Key Recovery is aimed at explaining the creation of the power hypothesis and the use of algebraic systems. The power consumed by a circuit varies according to the activity of its individual transistors and other components.
Tutorial B3-1 Timing Analysis with Power for Password Bypass. 22 Differential power analysis Differential Power Analysis DPA is a statistical method for analyzing sets of measurements to identify data-dependent correlations.